This entry was posted on Friday, February 26th, 2010 at 4:15 pm and is filed under Important Announcements. You can follow any responses to this entry through the RSS 2.0 feed. You can leave a response, or trackback from your own site.
26.02.2010 Post in Important Announcements
On July 17, 2009, October 1, 2009 and February 19, 2010 InstaForex Client Service has got reports from customers about unapproved e-mails from third persons not related to the company. There were the offers to follow the link and receive a bonus from InstaForex. Taking into account these three incidents, we recognize our responsibility to our clients and deem in duty to warn traders about possible fraud attacks. Hope, this article will help you to protect your computer and make you ready to break up phishing attacks.
Every day mass media publishes lists of organizations, whose clients were attacked by phishers. As soon as hackers work out new methods of attacks, business responds with developing of new clients’ personal data security facilities and gets external experts to take part in increasing safety level of electronic mail. In their turn, customers try to protect themselves from a stream of “official” e-mails and set stricter rules of communication.
While most organizations enhance severe rules of spam filtration, they should also take active measures in a struggle against phishing. Understanding the instruments and methods, used by fraudsters, and analyzing possible holes in perimeter’s safety, companies will be able to defend themselves against lots of popular and successful directions of such attacks beforehand.
Stealing sensitive information never has never been easier than nowadays in Electronic Technology Age. Hidden among trash of e-mails, avoiding most of anti-spam filters, new vector of assault is intended for thieving confidential personal data. Today professional criminals use specially formed messages to ensnare their victims. This type of attacks is called phishing.
By “phishing” we mean customers social engineering techniques used to steal their private information and confidential data transfer for a criminal use. Fraudsters use spam or computer-bots for their assaults. At the same time a size of a company-victim does not matter at all; quality of personal data weighs of its own accord.
Month by month phishing-swindles keep increasing not only in amount, but also in a quality manner. At present time a growing number of clients are attacked by phishers, such mass mailings are sent to millions of e-mail addresses all over the world. Moreover, some attacks are organized upon exact groups of clients. Using different methods of attacks, phishers can easily deceive clients for providing their financial data.
Most financial organizations, which business is related to the Internet, introduce new methods for saving clients private data. For example, InstaForex clients can enable service of SMS security: each time you are going to withdraw your funds from a trading account, you will need to verify the operation by protecting code, which will be sent automatically by the system to your mobile phone. So even if swindlers will get an access to your account, they will not be able to transfer your funds to their accounts. However, you should understand, that there are lots of easy instruments, which can be used by everybody for protecting against phishers. That is what I am driving at in this article.
First of all, some words about phishing technologies. These attacks combine methonds of technologic deception and social engineering. Phisher has to persuade a victim to make some actions purposely, which will provide an access to the sensible information. Nowadays hackers actively use the popularity of such means of communications as e-mail, IM, IRC and web-pages. In all cases phisher must impersonate a trusted source, for example, support service or administration of site, forum etc, to lend credibility to a victim.
Down to recent times, the most successful phining assaults were made via e-mail, where a phisher play a role of an authorized person, imitating his/her reference address of electronic e-mail or putting elements of corporate style. For example, a victim receives an e-mail from support@instaforex.com <support@instaforex.com> (an address is substituted) with a message line “modification protection”, where they ask his/her to follow the link https://secure.insta-forex.com/en/withdrawal.aspx <https://secure.insta-forex.com/en/withdrawal.aspx> (the domain belongs to the attacker, not the company; moreover, the Hypertext Transfer Protocol is not secured, it must be HTTPS) and enter his trading password.
Pic. 1. The example of phishing e-mail.
There could be much more methods, which phishers can use for stealing your sensitive data. They can send you a warning e-mail, that your account was hacked and you need to enter your trading password in a special form (there must be a fake link in the e-mail) for recovering it. Also they can offer you to get a bonus, and again an e-mail will contain a fake link to a false form. You can receive an e-mail with information about moving accounts to a new trading server and request of your personal data as well. Another way is sending e-mail with attached file or archive (such as exe, zip, rar), if a victim opens this file, his/her computer will be paralised by a trojan or virus.
Online phishing means copying popular sites by malefactors. They use similar domain names and analogous web-design. Then everything goes on according the used scheme. A victim, attracted by great bonuses, enters credit card and accounts numbers, pin codes and so on. All suspicions are dissipated, because the copied website looks like real. Such means of phishing has been in use during a long time. But little by little they become uneffective because of spreading knowledge about information security.
The third type is combined phishing. The point is in creating a fake site of a company, which victims are attracted to. They are offered to visit this website and do some actions by themselves. Usually hackers use methods of psychological effect.
Phishing attacks, organized via e-mail, are the most widespread. Implementing technologies of spammers, phishers can send out millions of e-mails to the real addresses in a few hours (or minutes, if they use distributed bot-networks). In most cases lists of e-mail addresses are bought by phishers from same sources as by spammers.
Using well-known defects in SMTP protocol, swindlers are able to make e-mails with a counterfeit “Mail From” line. They can set a name of any organization as a title of an e-mail. In some cases phishers can also set “RCPT To” box at chosen e-mail address, due to this a client’s reply to the e-mail will be sent to the phisher. Below is a list of methods used by phishers when operated at electronic mail:
– official form of e-mail
– copying valid corporate e-mail addresses with minor changes of URL
– HTML, used in electronic messages, complicates URL details
– standard attachment with worm or virus
– anti-spam filters complicating technologies
– fake links to popular blackboards and mailing lists
– counterfeiting “Mail From” line
Follow the simple rules and you will always be able to repel phishing attack.
Rule #1. Never reply to e-mails, requesting your private data.
Generally InstaForex support service send e-mail with personified compellation to a client. Phishers commonly use showy titles like: “Warning”, “Urgent”, “Your account was hacked”, “Specially for you!”. This is used for making a victim to follow a link immediately.
InstaForex never request account details or password via e-mail, only if a client has appealed to the company first. Even if an e-mail seems to you legitimate, you should not reply to it is better to call the company and specify. You should also carefully open attachments and download files from websites.
Rule # 2. Visit the company’s websites by entering its URL in a browser’s address bar.
Phishers use similar domains of the chosen company. But if you follow such link, you will come upon phishing web-page instead of real company’s site. This will not give you a full guarantee, but it can save you from some types of attacks.
Rule #3. Regularly check your account statement.
In case of discovering a suspicious transaction, immediately contact the company’s support service.
Rule #4. Check the security level of a site you are visitng.
Before you enter your sensible data at the company’s site, do some checks to be sure, that the company uses cryptographic methods. First of all, check the URL in an address bar. If you visit secure area (client and partner cabinets, account registration page, forms for depositing/withdrawing money and forms for getting the bonuses are situated at secured area), the address must begin with https://, not just usual https://.
 Pic. 2. Green color in address bar indicates safety of the official InstaForex website.
Pic. 2. Green color in address bar indicates safety of the official InstaForex website.
Secondly, check an icon with the image of lock in a status bar of your browser. You can check the cryptoprotection level, determined by the bit quantity, just clicking to this icon. Green address-bar of secured area of InstaForex website indicates high security level of a clinet’s data.
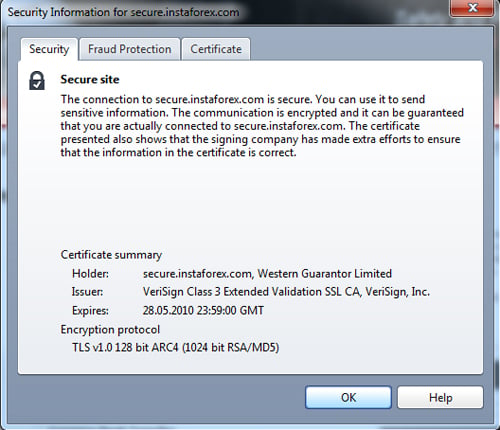 Pic. 3. How to check the cryptoprotection level.
Pic. 3. How to check the cryptoprotection level.
Rule #5. Be careful, while working with e-mail and confidential data.
Never use the same passwords for all your online-accounts. Never provide your pin codes and passwords to third parties.
Never open spam e-mails and never reply to them, because with this action you provide a valuable information to a sender, that he got a valid e-mail address.
Rely on common sense while reading a message in e-mail. If something seems too good and unbelievable to you, so probably it is.
Do not make boast of your big profit at forums and public communities. This information can be interesting for hackers and become a reason for organizing a phishing attack upon you.
Rule #6. Protect your computer.
The most effective protection from trojans is antivirus software. Set antiphishing filters in your browser. Do not forget to scan your system by antivirus program from time to time.
Rule #7. Always report about discovering a suspicious activity.
If you have received a phishing e-mail, always report this to the company. First of all, the company can confirm if this mailing was approved or not. Secondly, they can warn other clients about a possible threat.
Added by Alexander Kozyrev,
InstaForex technical specialist


